This error can occur in a topology where an ADFS server is used for authenticating to Office 365 and the CRM Online service.
When starting the CRM for Office 365 plug-in, the users receive the following error message during the ADFS authentication:
| An error occurred
An error occurred. Contact your administrator for more information. Error details
|
On the ADFS server, event 364 is logged in the Application log (note the highlighted part):
Log Name: AD FS/Admin Source: AD FS Date: <date> <time> Event ID: 364 Task Category: None Level: Error Keywords: AD FS User: adatum\<adfs service account) Computer: ADFSSRV.adatum.dk Description: Encountered error during federation passive request. Additional Data Protocol Name: wsfed Relying Party: urn:federation:MicrosoftOnline Exception details: Microsoft.IdentityServer.Service.Policy.PolicyServer.Engine.InvalidAuthenticationTypePolicyException: MSIS7102: Requested Authentication Method is not supported on the STS. at Microsoft.IdentityServer.Web.Authentication.GlobalAuthenticationPolicyEvaluator.EvaluatePolicy(IList`1 mappedRequestedAuthMethods, AccessLocation location, ProtocolContext context, HashSet`1 authMethodsInToken, Boolean& validAuthMethodsInToken) at Microsoft.IdentityServer.Web.Authentication.AuthenticationPolicyEvaluator.RetrieveFirstStageAuthenticationDomain(Boolean& validAuthMethodsInToken) at Microsoft.IdentityServer.Web.Authentication.AuthenticationPolicyEvaluator.EvaluatePolicy(Boolean& isLastStage, AuthenticationStage& currentStage, Boolean& strongAuthRequried) at Microsoft.IdentityServer.Web.PassiveProtocolListener.GetAuthMethodsFromAuthPolicyRules(PassiveProtocolHandler protocolHandler, ProtocolContext protocolContext) at Microsoft.IdentityServer.Web.PassiveProtocolListener.GetAuthenticationMethods(PassiveProtocolHandler protocolHandler, ProtocolContext protocolContext) at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
As stated, the “… Requested Authentication Method is not supported on the STS …” indicates that the ADFS service lack support for the authentication method requested by the CRM plugin.
In certain ADFS configurations, the administrator may not have enabled forms-based authentication, which prevents clients from logging in if their authentication process is based on this method.
To resolve this issue, change the ADFS configuration and add forms-based authentication to the supported authentication methods.
First, verify which authentication methods your ADFS service is configured to support:
- Open Server Manager on the primary ADFS for Windows Server 2012 R2 server
- Click Tools, and then click AD FS Management.
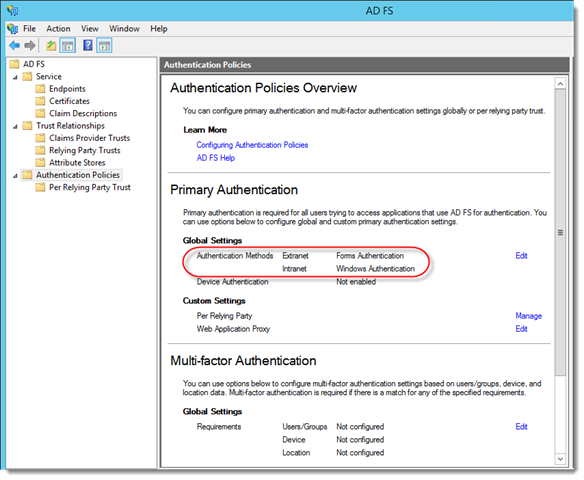
- In the AD FS snap-in, click Authentication Policies.
- Review the Global Settings in the Primary Authentication section.
- To support modern authentication, the Authentication Method for both Intranet and Extranet must have the Forms Authentication option enabled.
Follow these steps to enable forms-based authentication for both authentication methods:
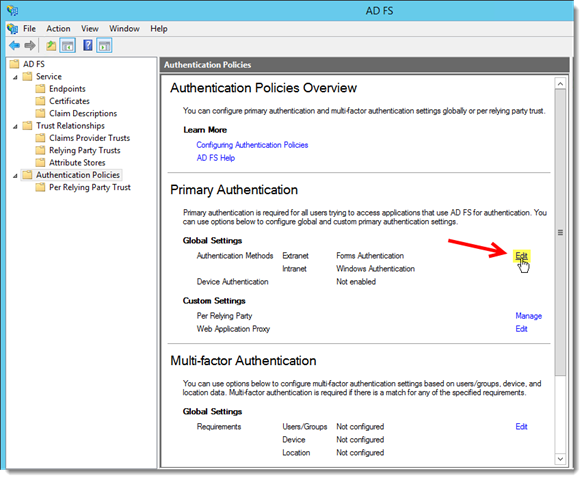
- In the AD FS snap-in, select the Authentication Policies branch.
- Under the Primary Authentication section, click Edit next to Global Settings.
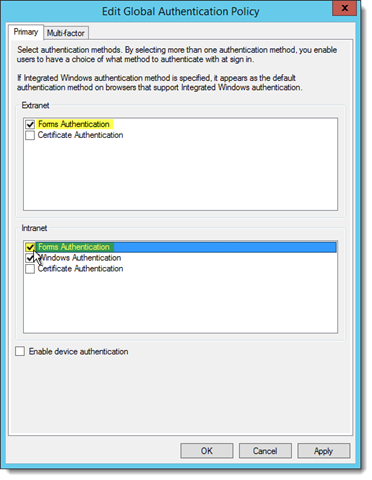
- In the Edit Global Authentication Policy dialog box, click the Primary tab.
- In both the Extranet and Intranet sections, ensure the Forms Authentication check box is enabled.
Click OK
Though it is not required, I recommend that you restart the ADFS service:
- Open an elevated PowerShell prompt on the primary ADFS server
- Run the following Windows PowerShell command:
Restart-Service adfssrv - Repeat this on any secondary ADFS servers
Futher reading: https://support.microsoft.com/en-us/kb/3015526